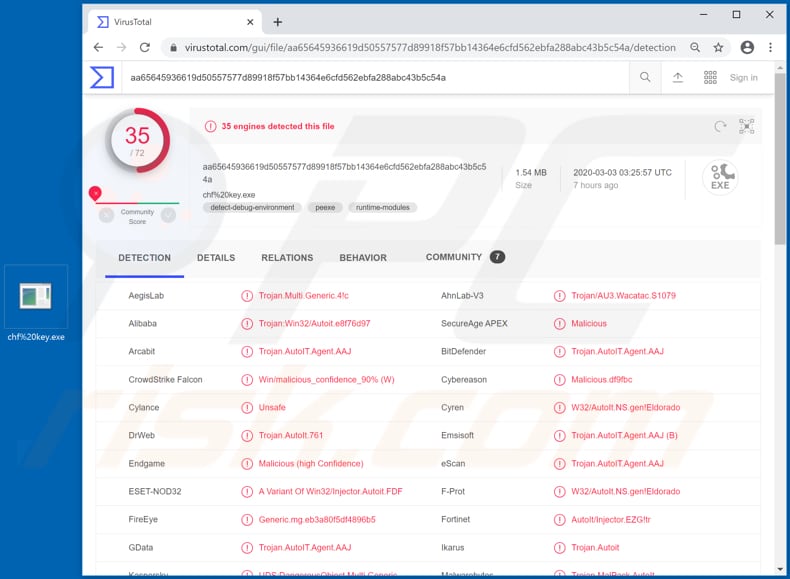
Invisibility Page. Options Page. Delivery Control Control Page.
Email Page. Protect your children online The web these days of full of dangers and inappropriate content that is just a few clicks away.
The more you know about your kids, the better you are prepared to get them out of trouble or prevent it altogether. Eavesdropping on your partner of spouse is irrefutably bad, but if you have a solid reason to suspect that your significant other may me involved into something, it never hurts to check.
Back up and recover lost text entries Ironically, a key logger can be used not only as spy software, but also as a tool that constantly records all text entries and can, if and when necessary, restore them. You can protect KidLogger with a password.
- top cell track program Motorola Moto G6.
- mobile location on Motorola Moto Z Play.
- Message tracking LG.
- need to spy on Galaxy S8.
A free security monitoring software that can be used as a keylogger. BlackBox works slightly differently compared to the other software on the list. You can monitor 1 local PC and up to remote computers in the network. Perfect for business means. BlackBox Express can log keystrokes, web searches, ran programs, visited websites and much more. The program is hidden by default, but you can still see it in the task manager. Very responsive and light on system usage.
It can record keystroke and has automatic log cleanup. You can protect the program with a password. To uninstall it, run the program, click on the question mark icon at the top right, go to Program end and select Uninstall.
keylogger wireless
It used to be for free, but the current version has turned into shareware with the program renamed to Actual Spy. The last free version 2. It can only capture keystrokes, however. This is the stealthiest option of all the above. Some keyboard loggers can be implemented entirely as hardware devices. The device stores signals from the keyboard, while everything appears to be working normally. If you keep your computer under a desk, the device would practically remain invisible.
Keyloggers Archives - Remove Spyware & Malware with SpyHunter - EnigmaSoft Ltd
The person can come back a couple of days later, grab the device and no evidence will remain. Good news is that there are no hardware keystroke loggers for mobiles, but both Androids and iPhones are vulnerable to keylogging software. Since modern phones use a touch screen, keyloggers adopt a specific approach.
- cellphone Telegram track Meizu Note 9.
- software to locate cell Samsung Galaxy M20.
- Simple Keylogger;
- KeyGrabber Module installation?
They eavesdrop on what you press on your screen. From there on, your camera, microphone, connected networks, devices, and all your messages are monitored. Anyone who has temporary access to your phone can load a keylogger. Your device can also get infected in the same way as a computer — via phishing emails and malicious websites.
RELATED POSTS
One of the most popular keylogging software for mobiles at the moment. You can monitor up to four devices from one account with the option to remotely read text messages. It is hard to detect and provides notifications and data quickly. You can also try a free demo version of the tool. This tool is easy to use, as the name suggests. This keylogger software does an excellent job of keeping call logs, browser history, social networking logs.
Captain Smiley is always on duty to protect your keyboard! But even he can have bad days at the office. For such days, he recommends reading on:. In general, you should be cautious when opening attachments. Keyloggers could be injected in files received through email, text messages, chats, networks, and even social media.
Pay attention to fishy emails, asking for your personal information. When used covertly inline devices are easily detected by a glance at the keyboard connector plugged into the computer.

Of the three types, the most difficult to install is also the most difficult to detect. The device that installs inside a keyboard presumably the keyboard the target has been using all along requires soldering skills and extended access to the keyboard to be modified. However, once in place, this type of device is virtually undetectable unless specifically looked for.
Remote Access software Keyloggers are local software keyloggers programmed with an added feature to transmit recorded data out of the target computer and make the data available to the monitor at a remote location. Remote communication is facilitated by one of four methods:.
Account Options
SpyHunter is a powerful malware remediation and protection tool designed to help provide computer users with in-depth system security analysis, detection and removal of a wide range of threats like Keyloggers as well as a one-on-one tech support service. Note: SpyHunter's scanner is only for malware detection. If SpyHunter detects malware on your computer, you will need to purchase SpyHunter's malware removal tool to remove the malware threats. Read more on SpyHunter.
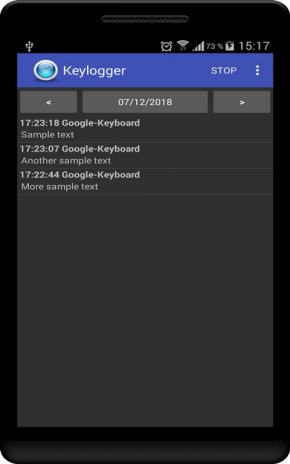 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
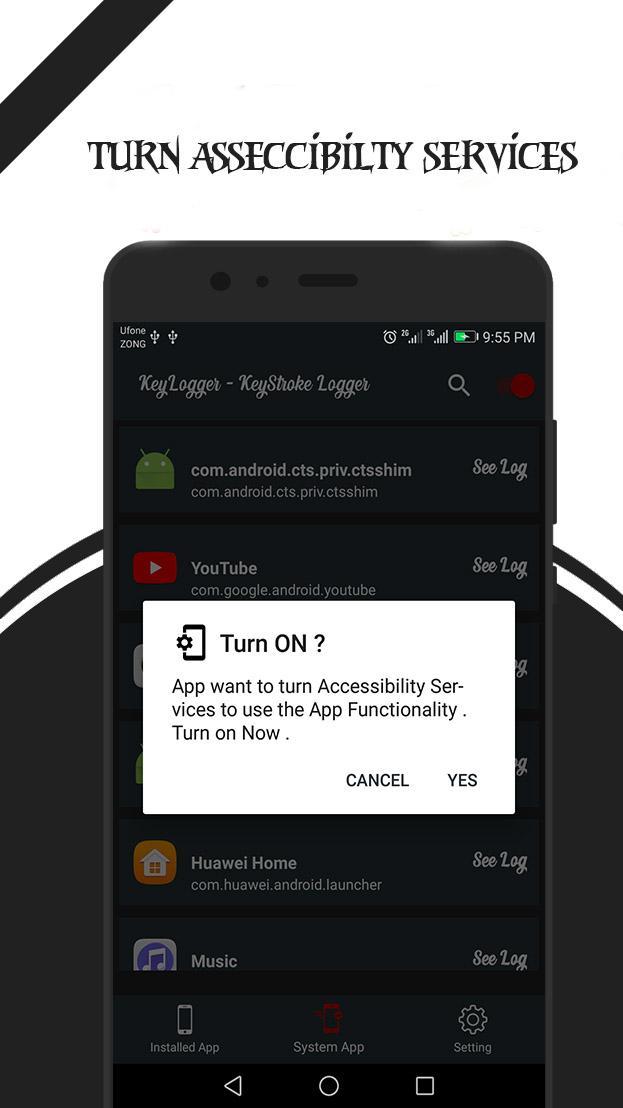 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
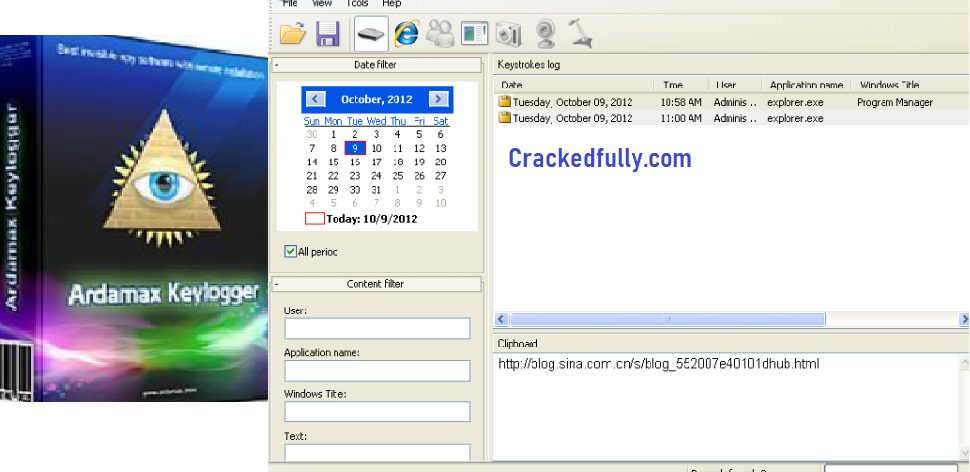 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
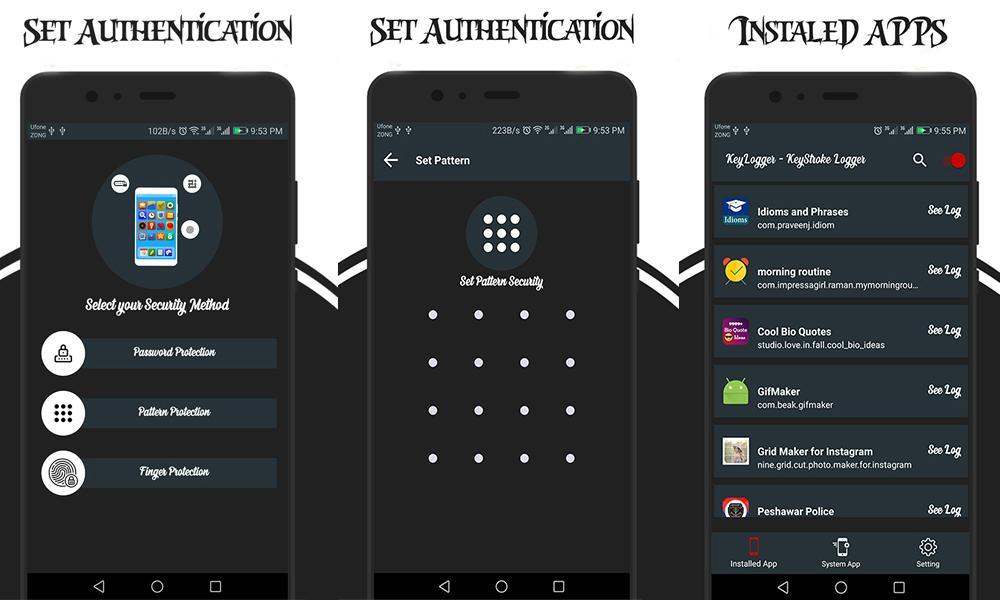 Xiaomi Redmi 6A keylogger
Xiaomi Redmi 6A keylogger
Related Xiaomi Redmi 6A keylogger
Copyright 2020 - All Right Reserved