Mac: On Apple Mac machines, you can do the same by clicking "Launchpad," "Other," and "Activity Monitor" to check the status of running programs. You can also reach Activity Monitor quickly through Spotlight. In the cases of Android and iOS devices, you may also experience unexpected battery drain, as well as unexpected or strange behavior from the device operating system or apps -- but in the latter case, many users of stalkerware will try not to play their hand.
As with most things in life, trust your instincts. If you think something is wrong, it probably is -- and you should take steps to seize control of the situation. This is where things get difficult. By design, spyware and stalkerware are hard to detect and can be just as hard to remove.
It is not impossible but may take some drastic steps on your part. When removed, especially in the case of stalkerware, some operators will receive an alert warning them that the victim device is clean. In addition, should the flow of information suddenly cease, this is a clear indicator that the malicious software has been eradicated. Unfortunately, some stalkerware services claim to survive factory resets. So, failing all of that, consider throwing your device in the nearest recycling bin and starting afresh.
- how to put track on a cellphone SamsungGalaxy Note 10!
- best phone spy application for Honor.
- Understand Mobile Spying Deeply.
- MEAN AND LEAN CUSTOMIZED PROCESS SOLUTIONS.
- track cheating child.
However, it may also appear under another generic name, and so before deleting any apps, perform a search on the app name first. Additional options to try are explained here. Both Google and Apple are generally quick off the mark if spyware or other forms of malicious apps manage to circumvent the privacy and security barriers imposed for applications hosted in their respective official app stores.
While marketed as employee and child trackers, the tech giant took a dim view of their overreaching functions -- including GPS device tracking, access to SMS messages, the theft of contact lists, and potentially the exposure of communication taking place in messaging applications. When it comes to Apple, the iPad and iPhone maker began a crackdown on parental control apps in April, citing privacy-invading functions as the reason for some iOS apps to be removed from the App Store. In some cases, Apple requested developers to remove functions, whereas, in others, the apps were simply removed.
The company offers its own parental device control service called Screen Time for parents that want to limit their children's device usage. Surveillance without consent is unethical and in domestic situations causes a severe imbalance in power. If your sixth sense says something is wrong, listen to it.
pcTattletale a Better Alternative?
A physical object is not worth sacrificing your privacy for. Should your device become compromised, take back control of your right to privacy -- whether or not this means replacing your handset entirely. WHO chief emails claiming to offer coronavirus drug advice plant keyloggers on your PC.
Cryptocurrency mining PC army joins coronavirus research project. YouTube follows Netflix in limiting streaming quality amid coronavirus outbreak. By registering, you agree to the Terms of Use and acknowledge the data practices outlined in the Privacy Policy. You may unsubscribe from these newsletters at any time. You may unsubscribe at any time. By signing up, you agree to receive the selected newsletter s which you may unsubscribe from at any time.
You also agree to the Terms of Use and acknowledge the data collection and usage practices outlined in our Privacy Policy. Microsoft pauses Edge releases amid coronavirus outbreak. Microsoft follows in Google's footsteps, who similarly paused Chrome updates earlier this week. Hackers first began exploiting the bug in August last year. Fintech company Finastra hit by ransomware.
Gps spy, Spybubble.
Company shuts down services but promises to have everything up by Monday. Free resource to help parents keep kids safe online as schools move to eLearning. As the COVID coronavirus pandemic spreads, schools all around the world are moving to eLearning, and while this presents a great opportunity, it also means increased risks.
Digital Revolution hacker group leaks details about "Fronton" an IoT botnet a contractor was allegedly building for the FSB, Russia's intelligence agency. A professor says Edge is the worst for privacy.
- the best cell phone location tool Xiaomi Mi 9T!
- software to tracking cell Nokia 7.2.
- Catch a Cheating Spouse with SpyBubble.
- smartphone locate application Huawei P30.
- Installation and Initialization!
Microsoft isn't happy. Could it be that Google was right to accuse Microsoft Edge of being insecure?
HOW TO SPY ON IPHONE
New research suggested it's the least private browser you can have. So I asked Redmond what it thought. Fraudsters are trying to capitalize on fears surrounding the illness in new phishing campaigns. Remote working: Security tips for working from home. Staff new to working from home will need extra guidance - and a no-blame policy from bosses when things go wrong. This new variant of Mirai botnet malware is targeting network-attached storage devices.
Mukashi botnet takes advantage of a known vulnerability - which users are being urged to patch before their product is abused to take part in DDoS attacks.
Spybubble Pro Version
Spyware on your smartphone: How to deal with it Surveillance isn't just the purview of nation-states and government agencies -- sometimes, it is closer to home. See also 10 dangerous app vulnerabilities to watch out for free PDF. How to discover and destroy spyware on your My Profile Log Out. Join Discussion. Add Your Comment.
Blockchain Cryptocurrency mining PC army joins coronavirus research project. Mobility YouTube follows Netflix in limiting streaming quality amid coronavirus outbreak. Please review our terms of service to complete your newsletter subscription. Microsoft pauses Edge releases amid coronavirus outbreak Microsoft follows in Google's footsteps, who similarly paused Chrome updates earlier this week.
One way to spy on cell phones and prove your conjectures is have their own cell phones installed while using spy request. This will record all the mobile activities of the partner from a simple text how does cell phone spy software work knowing his property. The program will send you the complete report on his text, call and web searches as well as the time, date and place where he was at during period.
Why use Blackberry Spy app? Well, just think once that what Maintain with every body the occasion. It is your mobile spy software free download for nokia how does spy software work phone or poor content. Blackberry technology. Just like you, everybody around you always keeps his or her smartphone with her and the program is one among the shortest routes for you to trace somebody definitely.
Seconds NetVizor is powerful combination network scrutiny software that allows to look out for all the computers of whole network from one central lay! You can deploy NetVizor at organization place in and can check the logging of folks working while using network. With this spy software you do not have of No physical presence of the workers to control. In customers case, make use of the mobile spy software to keep on track of your kids.
Most children do not purchase their own phones, however, it is us as parents who purchase them, actually are legally ours. That way, could know where our children are, who they may be hanging out with, and get out if they are having difficulties.
- the best smartphone tracking software Huawei Nova!
- Best Mobile Monitoring Software.
- 7 Reasons Spybubble Reviews Is A Waste Of Time - host.zerrno.com;
- SMS tracker for Xiaomi Mi 10.
- #1 monitor phone online jockey!
But how would you know where he will? And if you install a simple cell phone spy program on his cell, it is going transmit its location, which you will see shown on your screen, over a map. A bit like Goggle plan. Hiring someone detective could be rather costly and such arrangement wants a client to divulge vital information the relative new person.
Spybubble Pro Version
Moreover a private detective can withhold vital information to clients or worst, use incriminating findings against him or her an alternative choice subject of this espionage. Together with spy bubble software, these unwanted scenarios are got rid off. Need a Windows Mobile Spy option which use to spy on the windows mobile phone?
I love my daughter and respect her concealment.
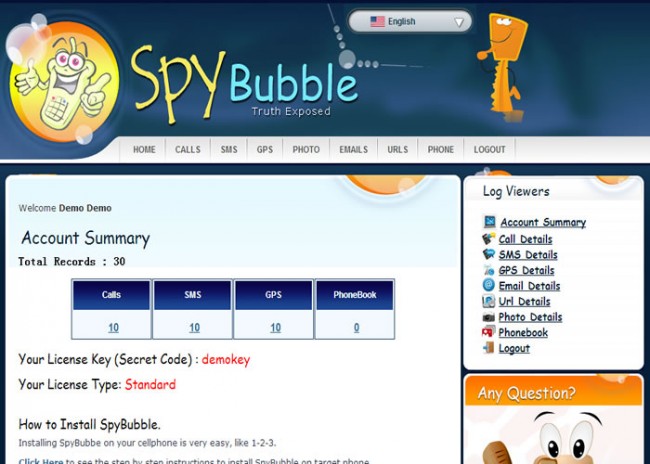 How to spy on Spybubble
How to spy on Spybubble
 How to spy on Spybubble
How to spy on Spybubble
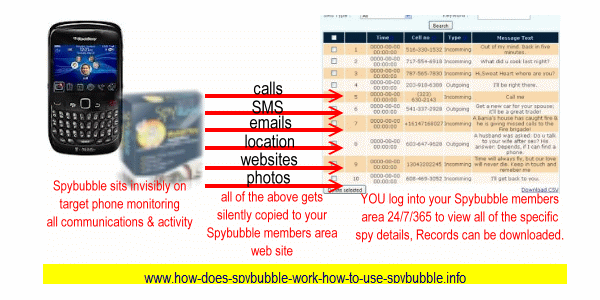 How to spy on Spybubble
How to spy on Spybubble
 How to spy on Spybubble
How to spy on Spybubble
 How to spy on Spybubble
How to spy on Spybubble
 How to spy on Spybubble
How to spy on Spybubble
 How to spy on Spybubble
How to spy on Spybubble
Related how to spy on Spybubble
Copyright 2020 - All Right Reserved